Executive Summary
The ReasonLabs research team has uncovered a widespread malware campaign that forcefully installs malicious browser extensions to over 300,000 Chrome and Edge users. These extensions range from simple adware to sophisticated data-stealing and command-execution tools. Active since 2021, this malware originates from fake download websites offering add-ons for online games and videos highlighting the persistent threat posed by malicious browser extensions.
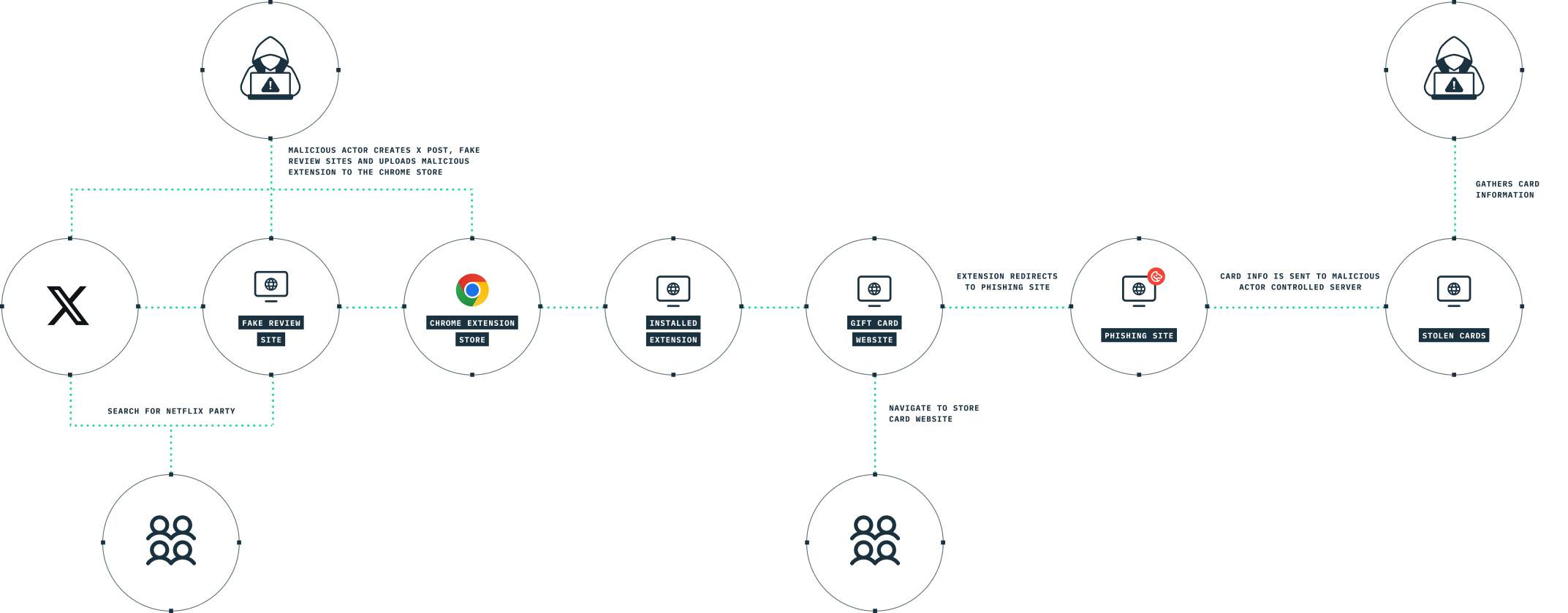
Malware Attack Pattern
Cybercriminals have created fraudulent download sites mimicking popular platforms like Roblox, YouTube, and VLC to distribute malicious browser extensions. These deceptive websites offer fake programs like "Roblox FPS Unlocker" to lure victims into downloading malware-laden installers. While some versions directly install malicious extensions, others use API-based downloads to deliver legitimate software alongside the malware, evading detection.
After a user downloads the program from the mimicked website, it establishes persistence by creating a scheduled task with a PowerShell script-like name, Updater_PrivacyBlocker_PR1, MicrosoftWindowsOptimizerUpdateTask_PR1, or NvOptimizerTaskUpdater_V2. This task is configured to execute a PowerShell script with a similarly deceptive name, such as -File C:/Windows/System32/NvWinSearchOptimizer.ps1. The PowerShell script then downloads a payload from a remote server and executesz it on the machine. Notably, the script is written to the System32 folder.
The attack cycle begins when the PowerShell script is executed. This script performs four key functions:
- Registry Modification for Forced Extension Installation: The script adds registry values to enforce the installation of extensions from the store under the following paths:
HKLM:\SOFTWARE\Policies\Google\Chrome\ExtensionInstallForcelist
HKLM:\SOFTWARE\Policies\Microsoft\Edge\ExtensionInstallForcelist
These extensions are designed to steal search queries and redirect them through the adversary's search engine. Additionally, the extensions cannot be disabled by the user, even with Developer Mode enabled. This method results in the browser displaying a message: "Your browser is managed by your organization." Newer versions of the script also disable browser updates. - Tampering with Browser Shortcut Files: The script modifies browser .lnk files to load a locally dropped extension. This local extension, like the one enforced through the registry, focuses on stealing search queries and can also communicate with a command and control (C2) server. The extension goes to great lengths to obfuscate its activities and cannot be detected on the "Extensions" management page, making it difficult for users to notice its presence.
- C2 Communication: The script establishes communication with a command-and-control server to report the status and receive instructions for the next stages of the attack. These instructions are downloaded and executed using invoke-expression. In this case, the script tampers with Chrome/Edge browser DLLs (e.g., msedge.dll), overwriting specific bytes to alter the browser’s search engine settings.
PowerShell Script Analysis
The PowerShell scripts connect to the C2 server to retrieve the following:
- Malicious Chrome and Edge Extensions: These extensions hijack search functions, with varying extension IDs depending on the specific attack.
- Local Extension: This extension downloads a series of files from the C2 server, saving them to a specified path provided by the C2 (in this instance, “C:\Windows\InternalKernelGrid”).
- Modification of Browser Shortcut Files: The script then modifies all browser “.lnk” files, altering the target path to include additional parameters such as “--load-extension” and others provided by the C2, including the base URL and “--disable-features=OutdatedBuildDetector”.
The script performs the following functions:
- addRegKeys
- addRegVal
- removeUpdates
- Main
The addRegKeys function is used to insert critical extension registry paths under HKLM\SOFTWARE\Policies. The malware ensures that the "ExtensionInstallForceList" is present for both Chrome and Edge.
The addRegVal function obtains parameter information from Stage 3 of the malware, following communication with its C2 server for additional installation directives. The C2 response contains various variables, and this function uses them to determine which extensions to forcibly install and the registry path for the force installation key.
The script contacts the C2 server using a unique UID and receives execution parameters in return. These parameters include the file storage location, specific files to download, extensions to install, arguments for the modified “.lnk” target, version number, restart instructions, and, crucially, a download link for the Stage 3 script.
The script disables all browser updates to prevent the restoration of default settings during each update, which would otherwise disrupt the malware's activities.
In the final stage, the script modifies browser shortcut “.lnk” files, downloads external files, and executes the subsequent stage script. It retrieves the installation directory from the C2 server ($CLocalPath) and checks if the extension is already installed and whether its version differs from the latest version specified by the parameter “v.” The script then recursively searches all “.lnk” shortcut files under the “C:\” directory. For shortcuts pointing to chrome.exe or msedge.exe, it injects the parameters provided by the C2 server.
Extensions linked to this campaign are:
Eliminating Extension Trojan Malware
To effectively eliminate this threat, users must manually remove the malicious extension and its associated components, including scheduled tasks and registry entries.
Deleting the Scheduled Task
- Open the Start menu or press the Winkey.
- Type “Task Scheduler” and select it from the search results.
- In Task Scheduler, click on “Task Scheduler Library” to display all tasks on the machine.
- To identify the malware task, look for the following characteristics: some text
- Click on a task from the list to view its details in the bottom half of the screen.
- Navigate to the “Actions” tab.
- In the “Actions” table, check if the “Details” field contains a path to “C:\Windows\System32” and references a PowerShell script (file ending in “.ps1”), such as C:\Windows\System32\Printworkflowservice.ps1”.
- The task name is often like the PowerShell script name.
- Once the malicious task is identified, right-click on its name.
- Select “Delete” to remove the task.
Deleting the Registry Keys
- Open the Start menu or press the Winkey
- Type “Registry Editor” and select it from the search results
- Navigate to: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome\ExtensionInstallForcelist.
- In the right pane, you’ll see a list of extensions with numerical values as “Name” and the ExtensionID as “Data”.
- Right-click on the extension name and select “Delete”
- Next, go to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Google\Chrome\ExtensionInstallForcelist and repeat the deletion process.
- For Edge extensions, repeat the same steps at the path: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge\ExtensionInstallForcelist
Manual removal of malware components
At this stage, the malware should no longer run, and the browser should be free from rogue extensions.
To remove the malware files, users are advised to follow these steps:
- Based on the IOCs list provided earlier, search your computer for the relevant folders and PowerShell scripts. Once found, right-click and select "Delete."
- Open the Start menu or press the Winkey.
- Type “File Explorer” and select it.
- Click on “This PC” and then on the Windows drive (or the corresponding drive letter).
- Navigate to “Windows → System32”.
- Search for a PowerShell script that matches one of the names from the IOCs list.
- Right-click on it and choose "Delete."
- Return to the “Windows” folder.
- Search for a folder name that matches one from the IOCs list.
- Right-click on it and select "Delete."
Conclusion
Malicious browser extensions pose a growing threat to online security. Cybercriminals leverage these extensions to steal data, infiltrate systems, and disrupt operations. Users must remain vigilant and employ robust security measures to protect themselves. To protect against these threats, users should consider using next-generation antivirus software like RAV Endpoint Protection or advanced security tools like the Online Security browser extension, which offer defenses against malware, identity theft, and more. Additionally, antivirus providers and endpoint protection software developers must prioritize these emerging threats to ensure the security and privacy of their users.
Sources Cited
- https://reasonlabs.com/research/new-widespread-extension-trojan-malware-campaign
- https://thehackernews.com/2024/08/new-malware-hits-300000-users-with.html
- https://www.bleepingcomputer.com/news/security/malware-force-installs-chrome-extensions-on-300-000-browsers-patches-dlls
- https://timesofindia.indiatimes.com/technology/tech-news/300000-plus-google-chrome-and-microsoft-edge-users-hit-by-dangerous-extensions-how-to-know-if-you-are-safe-or-not/articleshow/112498829.cms
- https://mspoweruser.com/how-come-300k-chrome-edge-users-got-hit-by-this-new-malware-heres-what-you-need-to-know
Get Notified
BLOGS AND RESOURCES

.png)
.png)





